Your sensitive data still needs to be shared. Share confidently with Keyavi.
Traditional data security creates so much friction that team members resort to sharing sensitive data unsecured to get the job done faster. Stop compromising security for productivity with Keyavi.
Digitally sharing data is inherently risky.
When sharing sensitive information, organizations face a difficult reality. Bad actors are constantly trying to access valuable data, while traditional security solutions create so much friction that they’re often bypassed. Once data leaves the network, organizations lose visibility and control, leaving them vulnerable to breaches, fines, and reputational damage.
We understand your data security challenges.
We understand the struggle between effective collaboration and data security. You probably face this everyday. Traditional security approaches simply place barriers around information, creating frustration when legitimate sharing needs arise. Keyavi takes a fundamentally different approach. By embedding intelligent, policy-based protection directly into each file, we enable secure sharing without compromising the efficiency of how people work together today.
- 15 global patents for our revolutionary technology
- HIPAA compliant for healthcare data protection
- Veracode Level 4 certified for application security
Now your data can protect itself around the globe.
Real-Time Control
Maintain complete control over your data, no matter where it’s stored or shared, forever. Update permissions instantly, even after files leave your network.
Advanced Forensics
Track every access attempt, policy change, and violation in real-time for deeper security insights and comprehensive audit trails.
Location Enforcement
Geofence your data to ensure it can only be accessed in authorized locations, preventing unauthorized access from suspicious regions.
Immediate Policy Updates
Modify access permissions anytime, even after your data is shared. Revoke access instantly when needed.
Time-Limited Access
Set files to automatically expire when they’re no longer needed, reducing risk without manual intervention.
Granular Usage Controls
Define exactly how your data can be used – restrict printing, editing, screen sharing, and more based on user identity and context.
Why You Need This
Control shared data
Once shared, data typically circulates freely with no way to manage who accesses it or where it goes. With Keyavi, organizations retain complete visibility and control, regardless of location. Update access policies in real-time, restrict sharing, or revoke access entirely – even after data has left the network. Whether dealing with misdirected emails, insider threats, or lost devices, the data remains protected and adaptable to changing circumstances.
Know everything about your shared data
With traditional data sharing, you’re in the dark – no way to see who’s accessing your files, where they’re going, or if someone’s trying to break in. Keyavi changes that.
Get real-time insights into every access attempt – whether successful or not –including who, where, and on what device. With a clear view of your data’s journey, you can spot risks before they become breaches and make smarter security decisions without the guesswork.
Protect data at its core
With Keyavi, security isn’t just applied to your data – it’s embedded inside it. Multiple layers of AES-256 encryption with rotating keys keep it locked down, while built-in access policies put you in charge. Define who can open a file, when, how, and even where with geofencing, ensuring your data stays put – whether that means within a specific country or city. Even if your files are stolen, shared, or leaked, they remain completely inaccessible to unauthorized users. Because with Keyavi, your data follows your rules, always.
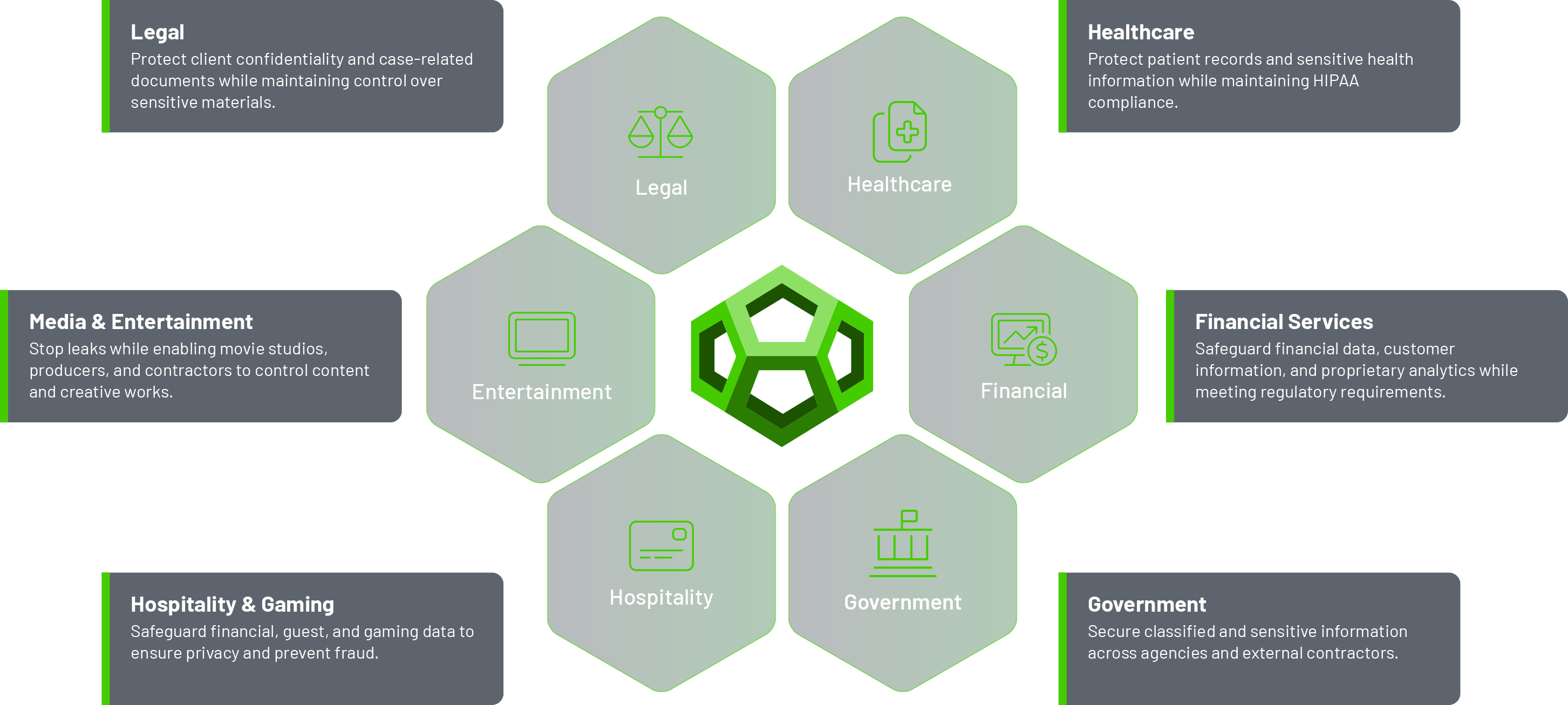
Supporting critical industries with advanced data protection
Distinguished for Superior Data Protection
The industry is taking notice of our paradigm shift to the future of data security.

2023 INFOSEC Innovator Winner
Visionary Market Maker, Self-Protecting Data

2022 GLOBEE Awards Gold Winner
Cyber Security Global Excellence

Next Big Things In Tech 2021
For giving data a mind of its own

2021 CISO Choice Award
For reshaping the very nature of the data security industry

2021 Cyber Defense Award
Black Unicorn Award for Cybersecurity Startups

2021 INFOSEC Winner
Global Infosec Award for Cyber Defense
Sharing Securely with Keyavi is Simple
Initial Setup
01
Your system administrator works with Keyavi to establish organization-wide policies and user accounts.
Easy Installation
02
Install our email plugin (Outlook or Google) for each team member who needs to share sensitive data.
Seamless Protection
03
Send emails like normal with an attachment and click the Keyavi Protect button – that’s it.
Secure Access
04
Recipients authenticate themselves before accessing information, giving you complete control and visibility.
The real cost of unsecured data sharing
Data breaches cost organizations an average of $4.5 million in direct losses, regulatory fines, and operational disruption. Beyond financial impact, breaches erode customer trust and market position. Security incidents triggered by improper data sharing often lead to internal investigations and business disruptions lasting months. Keyavi mitigates these risks by maintaining control of data, regardless of where it travels.
Join the data security revolution
Keyavi customers transform their approach to data security. Instead of restricting collaboration, they enable it. Instead of losing visibility when files leave their network, they gain unprecedented insights. Our clients often report faster business processes, reduced security incidents, and increased confidence in their data protection strategy.

