
Manufacturing
Overview
Manufacturing firms face significant challenges associated with the loss of intellectual property (IP), trade secrets, and research & development (R&D) information through cyber espionage and data breaches, both intentional and accidental. In 2022, the manufacturing industry was the hardest impacted by extortion attacks with 447 victims being reported on Data Leak Sites (PaloAlto, 2023). Whether attacks originate externally from nation state actors and cybercriminal syndicates or internally from trusted insiders, data loss not only affects their own revenue and reputation, but may also adversely impact national security, critical infrastructure, and global economic strength.
Modern manufacturing requires collaborative supply chains throughout the entirety of the product manufacturing lifecycle, increasing the risk of data loss. Not only do firms need to protect their data within their environment, but they also need to trust that their data is being protected beyond their perimeter and outside of their control, by their vendors and suppliers. “Trust” of course isn’t a security mechanism – the paradigm of managing risk in the supply chain must shift to enable organizations to protect their data wherever it goes, forever.
Situation & challenge
A global manufacturing firm had an opportunity to win a highly lucrative contract as a supplier for a third-party engineering firm and aimed to differentiate themselves as the most secure vendor for the job. As part of this potential project, the manufacturing firm’s engineers on the factory floor would be handling the sensitive information, such as schematics and engineering drawings, belonging to the third-party. With various regulations and standards at play to ensure the protection of the highly sensitive information (such as EAR99, NIST, and soon, CMMC), the firm needed to demonstrate why they were the best choice to fulfil the contract, while minimizing internal friction and costs.
Ensuring that front line workers were able to seamlessly access critical data with no disruption to their typical workflow was essential for keeping costs down and maintaining efficiency and productivity. An easy to use, yet robust mechanism for multisite comprehensive data protection seemed like an impossible task given the typical trade-offs.
Previous attempts of legacy approaches to lockdown data, such as by using data loss prevention (DLP) technologies had proven difficult to manage and highly disruptive to factory operations. DLP’s perimeter-focused approach failed once sensitive files left the network, which is challenging to address in their multisite multiparty supply chains. Once the data was gone, it was gone for good with no control, protection, or visibility. Additionally, the complex configuration and management at the administrative level, in addition to slow performance, disruption to business processes, and excessive false positives resulting from DLP forced the firm to seek new solutions to combat data loss.
Solution
Using Keyavi, the manufacturing firm successfully won the multi-million-dollar bid, demonstrating the exceptional care that they were taking to protect their partner’s sensitive information with a zero-trust and data-centric approach. Keyavi provided them with a solution that enabled real time policy-based data access control in perpetuity, supported by industry-standard encryption.
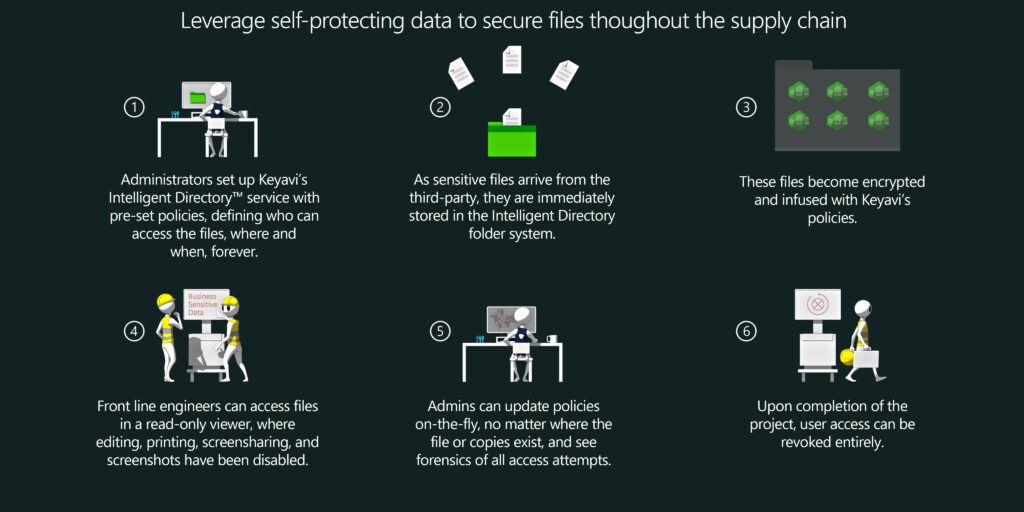
By implementing Keyavi’s self-protecting data, the risk of insider threat, where workers may attempt to copy or share the files with others or their own personal accounts, is eliminated. Access is restricted solely to those authorized and within the confines of the policies (such as geolocation and time-window) set by the administrators, allowing the firm to meet requirements dictated by ITAR, EARS, and others.
For additional security and investigations, administrators are now able to leverage existing SIEM and SOAR functionality built into Keyavi-protected data and also integrate the Keyavi chain of custody forensic transactions directly into their existing SIEM/SOAR tool. Admins can view details of every access attempt, whether successful or not, and drill into the forensics of each attempt in these chain of custody logs. When the project is complete, access to the files (including any copies made) can be revoked entirely, satisfying access control and retention requirements.
The firm successfully shifted the paradigm by using Keyavi to infuse security into the data itself, allowing the data to become self-protecting and intelligent, with perpetual security, control, and visibility whenever it went. Selfprotecting data eliminated the complexity associated with legacy protection measures, while allowing for seamless usage by factory floor workers to keep productivity up. As Keyavi’s cutting-edge data protection is being introduced across the industry, gaining that competitive edge and confidence that your data – and your third-party’s – is secure will set you apart and you can focus on your own innovations, productivity, and revenue.
