
Data Loss Risk Mitigation & Self-Protecting Data
Protecting your data across every platform, every application and every access attempt
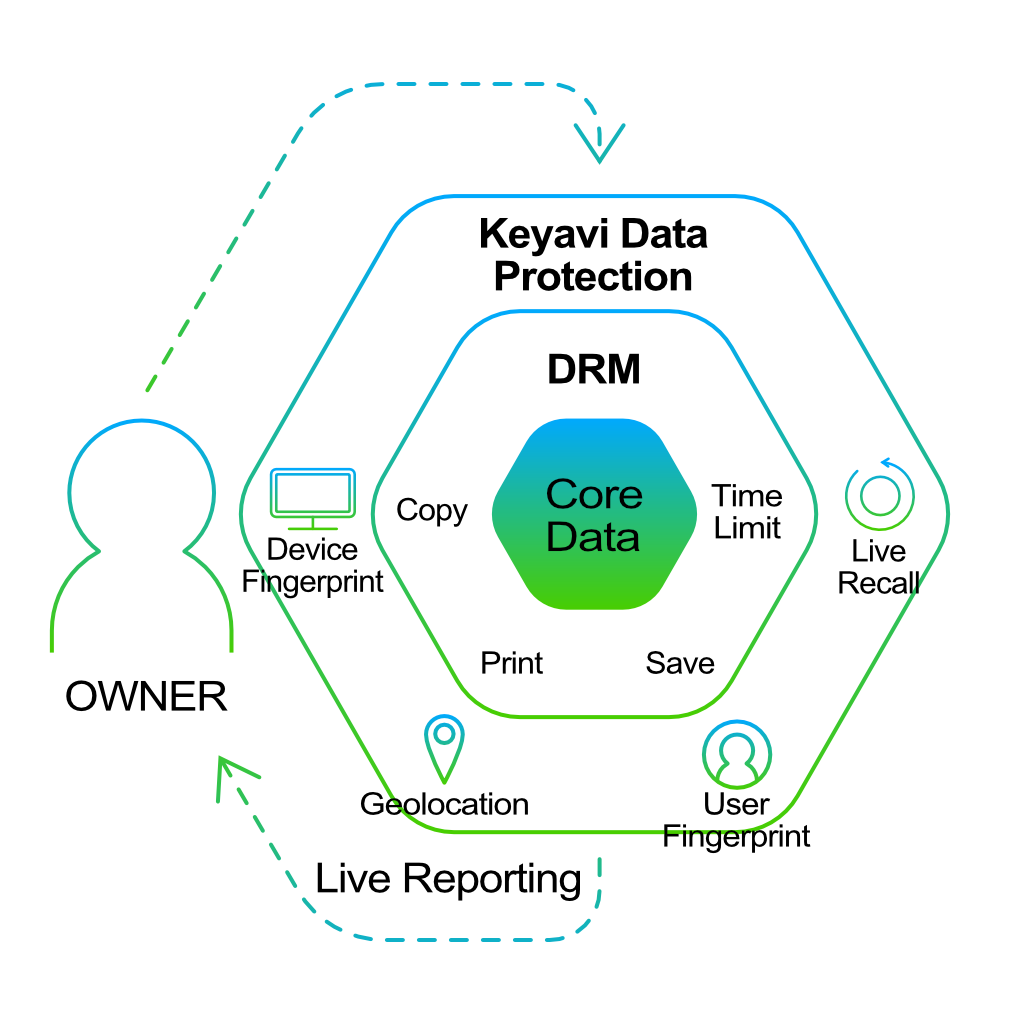
Many organizations rely on DRM for the trusted exchange of digital information over the Internet whereby the user is granted only the privileges that the document sender allows (Gartner, 2020). While DRM provides many excellent security features, it also leaves many data security gaps open. By its very definition, its proprietary to the platform it is on, whether that platform is Microsoft®, Adobe® or others. It would be a rare organization that maintains all of its data, files and information in a single platform in today’s world.
Modernize your DRM strategy with self-protecting data
DRM data security gaps
DRM provides no inherit protection for the data itself. Additional protection is needed to protect when data and files are lost, leaked or stolen. Even the more robust DRM solutions like Microsoft and Adobe offer single layer or minimal protection. Single-layer encryption can be easily cracked by a determined and patient hacker, leaving the organization’s critical data at risk for extraction, corporate espionage and extortion, damaging the organization.
Keyavi complements and works collaboratively with any and all existing DRM solutions. Keyavi adds additional policy sets and access controls to secure the DRM security gaps. When the Keyavi-protected data determines it is allowed to be accessed under current conditions, that data is still a DRM-enabled file. Because Keyavi infuses protection into the data for all file types no matter where it goes or how it is shared, it can be used to complement or replace DRM altogether.
DRM limitations
DRM solutions require a central root certificate system for all parties to trust. This means that for company A to share information with company B, the only way to decrypt a file is for company A to trust the PKI certificate of Company B or the intermediary platform, whether that is Microsoft, Adobe or other.
With Keyavi, your trust environment is infused into the data itself so there is no requirement for sharing root trust.
Unique Keyavi capabilities
Platform- & transport-agnostic: Embeds into the data itself, completely independent of any delivery method
On-the-fly policy editing: Implements owner’s policy changes, including authorized users and devices, time periods and geolocation every time the data is accessed
Chain-of-custody & compliance reporting: Captures and records access attempts through the service with unique user and device information and geolocation
Advanced embedded data protection: Patented, multi-key encryption technology protects data anywhere it goes for any length of time
| Features | DRM | Keyavi |
|---|---|---|
| Copy | X | X |
| X | X | |
| Save | X | X |
| Time embargo | X | X |
| Collaborate | — | X |
| Geolocation control | — | X |
| Identity fingerprint | — | X |
| Device fingerprint | — | X |
| Real-time policy editing | — | X |
From Digital Rights Management to Data Rights Management
Whether you are currently using DRM or not, you can now completely protect your data and keep it under your control, forever, even after it leaves your possession. To learn more about self-protecting to complement or replace your DRM, join us today for a demo and more information.





